Marketing Agencies - Outsource Your SEO To Top Sydney White Label SEO Company - we will give you wholesale rates. All work done by expert Australian SEO based in Sydney - nothing overseas.
100% SAFE and fantastic results - call now on my private mobile 0404 028 559Increase Your Digital Marketing Agency’s Profits
We will supply you with the fastest & most cost-effective way for you to increase your agency’s profits and you won’t even need to hire any new staff – just resell our SEO services to your clients.
The White Label SEO Packages from Sydney Search Results can provide you with a virtually passive income stream every month.
If you have a web design company, a digital marketing agency or even an SEO company and right now you are letting precious business go elsewhere just because you don’t offer any type of SEO service or are finding it difficult to achieve results, we can give you what you need.
When clients request SEO and you simply cannot provide it, what happens? Do you currently just refer them on, leaving money on the table? Well you could offer your clients the full range of digital services including SEO even if you cannot provide SEO in house and don’t wan’t to employ new staff.
Call me today on (02) 8005 0339 and find out what we can do for you.
David Cannell, SEO Strategist.

We Can Rank Your Clients’ Website While You Take The Credit And Make More Passive Profits.
Let Us Show You How Your Clients’ Competition Are Taking Their Business Leads & Customers And How Your Agency Can Take The Credit For Bringing More Business To Your Clients’ Websites.
We Are Experts In Providing White Label Outsourcing Services For SEO.
1) I am David Cannell the business owner and an SEO outsourcing expert with over 14 years successfully marketing businesses online for digital agencies, call me on my mobile 0404 028 559 and I will discuss your SEO projects with you and do the competitive analysis that will show you what leads your clients are missing out on.
or
2) Simply fill in the form and I will get back to you within the hour – not with an auto responder but with a personal email including a detailed report on the traffic your website is currently missing out on. Traffic which your competition are getting and converting into sales.
 Please provide us with your contact details so that we can get back to you within the hour during business opening times and by the next morning if you enquire after hours.
Please provide us with your contact details so that we can get back to you within the hour during business opening times and by the next morning if you enquire after hours.
Also, if you wish for us to take a look at your project before we speak, please supply your client website address so that we can have a look at their website, analyse their market, check their current rankings, and do the analysis on the top performers in their niche including what keywords they rank for and where their traffic to their website is coming from, so that when we get back to you we can have an informed discussion about your project. Don’t worry about client confidentiality – we are happy to sign an NDA agreement with you that legally binds us to NEVER contacting any of your clients directly.
Knowing which competitive keywords your competition is ranking for and which of those keywords is driving the highest % of traffic to their website means that YOU can target those keywords and grab those leads. Find out more about my 14 years of successful SEO business online here.
We will provide you with:
- wholesale prices for bulk orders
- full ranking tracking platform that you can login to and monitor your clients rankings
- white label reporting so you can send out branded reports to you clients
- exceptional service
- outstanding rankings – we are confident that we will get your clients better, faster and most importantly safer rankings than any other seo outsourcing solution
- affordable prices
- the opportunity to form a long term business relationship with a service provider with and outstanding reputation and an exceptional track record for results
I guarantee that YOU, the business owner or manager will only ever deal with ME, the SEO expert and business owner for ALL your client projects. I am able to show a full portfolio of results we currently achieve with white label SEO on receipt of a non compete, non disclosure statement from you.
We won’t give you a sales pitch, we will come back to you with a real analysis of how we can help you grow your business. And remember, we have no lock in contracts, we invoice on a month to month basis, you are free to cancel any time.
Our Guarantee: try us for one month, and if at the end of the first month you are not happy with the progress you are making we will refund you in full – no fine print, no questions asked.
In fact, for agencies we are willing to work on one of your client projects for one month without payment so that you can see the outstanding results we can achieve even within the first month of a job. If you are impressed with our work, we can then discuss terms to continue on the job, and hopefully take on many more of your clients.
The 7 Things You Should Know Before Hiring An SEO Company In Sydney or Anywhere In Australia – Even More So Now In 2015
Listen to our website and business owner David Cannell discussing: what every business owner should know before hiring and SEO company.
“The 7 Points YOU Need To Ask Any SEO Company BEFORE Employing Their Services.”
Knowing what to ask could potentially save you a lot of wasted time, money and opportunity when engaging an SEO company. We tick all the boxes covered in the video. Do other SEO companies?
So after watching the video give call us on (02) 9314 3224 or fill out our contact form on the right and compare us.
Try Our Services For One Month And You Will See Why Our Clients Love Our Results.
Still Worried Whether SEO Still Works? Read Our Full Explanation Of What Business Owners Need To Understand If They Want To Avoid Being Penalised By Google For Poor Quality SEO.
Do your background check due diligence and Google me by clicking here : David Cannell SEO or here David Cannell Online Reputation

Case Study – would your clients want results like these for national level keywords in an ultra competitive market?
Brief: Increase sales in a highly competitive adult pharmaceutical market.
Our client is a Sydney based pharmaceutical eCommerce site. After years of working with SEO companies that were not performing, they came to Sydney Search Results because they wanted to grow their business through a more effective search engine optimisation campaign.
Solution:
The project started by developing a content strategy that positioned them as an authority in their market.
The site was developed with a strong need for converting new online visitors into customers. During the campaign we implemented a strategic ‘on-site’ SEO plan of action that was consistent with the overall marketing strategy and a promotion campaign to push them to the top of Google. The brief: to drive as much traffic to the website as possible through an organic SEO ranking and convert them into sales.
Results:
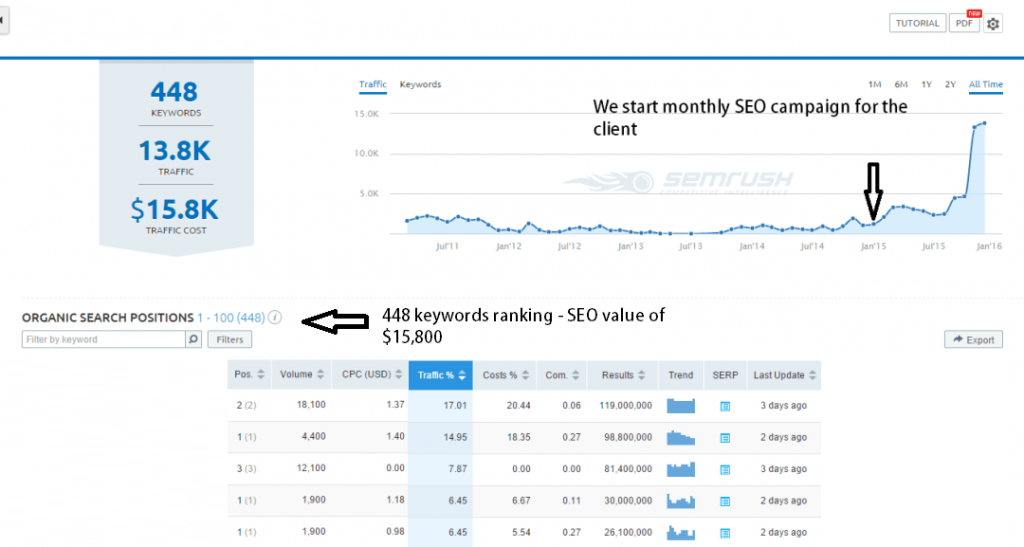
Within 3 months of the website being promoted by us, our SEO expert had achieved page 1 rankings in Google for most of their most highly searched keywords. Then within six months they had completely dominated their market whole: ranking as the number one commercial site in their niche in Google. Yes, #1 in the search results for keywords which included the NUMBER ONE HIGH TRAFFIC KEYWORD in their market and other high volume search terms. Traffic from SEO increased massively and sales rocketed.
We can discuss the details of this project – and other successful projects with you on (02) 9314 3224
Things to Consider when Outsourcing SEO To A White Label SEO Provider
Search engine optimisation isn’t the simplistic activity that it once was, in fact over the past few years it’s become one of the most extensive topics to be involved in – let alone keep on top of. Many businesses offering these types of services find that dealing with the intrinsic requirements and stringent policies proposed by search engines can be as time consuming as they are challenging. Fortunately, there’s always the option of outsourcing to a white label SEO provider, but how can you be sure that you’re picking the right company?
First things first
If you’re going to rely on a third party to represent the quality of services that your company emanates, then the chances are that you will want to keep things as close to home as possible. Local experts may cost a little more than lesser-experienced equivalents, but the reassurance that comes from hiring a professional will be rewarding well into the future.
Where cheaper companies might offer services that appear good on paper, in reality they are often only able to stay so cheap because they use risky tactics. It’s these tactics that can lead to penalty and complete de-listing if the offences are considered that severe. A local expert on the other hand will already have a firm grasp of the market and will be able to utilise the most effective techniques available.
Check a companies’ reputation
If you like the look of a potential partner, then the next thing to do is to get to know their background. What do their clients think? What are they offering? How successful are they at what they do? If they don’t tick all of the right boxes then it may not be worth investing your time or hard earned cash.
The whole point of outsourcing your services is to free up your time without having to worry about losing clients. If your third party isn’t up to the job, then it will be your organisation in the firing line. Think carefully before signing on the dotted line, especially if you intend to keep your clients happy. The greater the level of service that you receive, the better services your clients can expect.
Keep things local
As mentioned above, relying on a local provider boasts a whole host of advantages. For a start, you will be able to relax in the knowledge that you’re in the same time zone as your third party. This will make getting in touch easy, whilst eliminating the need to wait for 12 to 24 hours for a response. There’s also the guarantee that you will speak the same language as your provider, minimising misunderstandings.
Possibly the most beneficial feature is the type of expertise that you will be able to turn to. Local services will have the same type of knowledge as you, as well as being able to utilise similar resources. The result? A service that mimics yours as closely as possible, without having to sacrifice quality for affordability.



